Secure And Efficient RemoteIoT Access With Raspberry Pi
RemoteIoT Platforms have revolutionized the way we interact with IoT devices, offering seamless and secure remote access without the complexity of managing SSH keys. As IoT continues to expand, the demand for robust and secure solutions grows. With Raspberry Pi, a versatile single-board computer, you can establish a powerful setup for remote operations, simplifying device management without sacrificing security.
In today's digital landscape, remote access solutions play a critical role in managing IoT devices. Whether for personal or business use, the ability to control and monitor devices remotely enhances efficiency and reduces operational costs. RemoteIoT platforms, when combined with Raspberry Pi, provide an affordable and powerful solution. This comprehensive guide will explore everything you need to know about RemoteIoT platforms, SSH key-free access, and setting up Raspberry Pi for secure remote access, catering to both beginners and advanced users.
This guide delves into the intricacies of RemoteIoT platforms, offering detailed insights into SSH key-free access and Raspberry Pi integration. It provides practical advice and actionable steps to help you establish a secure and efficient remote IoT management system. From understanding the basics to exploring advanced configurations, this guide ensures you're well-equipped to harness the full potential of IoT technology.
Read also:Will Dan And Serena Get Back Together Exploring The Possibilities
Table of Contents
- Exploring RemoteIoT Platforms
- Understanding Raspberry Pi
- The Importance of SSH Key-Free Access
- Step-by-Step Setup Guide
- Enhancing Security in RemoteIoT Platforms
- Advantages of RemoteIoT Platforms
- Overcoming Common Challenges
- Practical Use Cases
- Best Practices for Deployment
- Emerging Trends in IoT Remote Access
Exploring RemoteIoT Platforms
RemoteIoT platforms are designed to facilitate secure and efficient remote access to IoT devices, enabling users to monitor, manage, and control their devices from anywhere in the world. These platforms leverage cloud-based infrastructure and advanced security protocols to deliver reliable solutions for businesses and individuals looking to enhance their IoT capabilities. By integrating with various hardware devices, including Raspberry Pi, RemoteIoT platforms allow users to create customized solutions tailored to their specific needs.
Beyond remote access, these platforms often include additional features such as data analytics, automated alerts, and customizable dashboards. These functionalities empower users to gain deeper insights into their IoT ecosystems, enabling data-driven decision-making and optimizing operational efficiency. Whether managing a home automation system or monitoring industrial equipment, RemoteIoT platforms streamline IoT management and enhance overall performance.
Understanding Raspberry Pi
What is Raspberry Pi?
Raspberry Pi refers to a series of compact single-board computers developed by the Raspberry Pi Foundation. Originally designed to promote computer science education in schools and underserved regions, these devices have evolved into versatile tools for a wide range of applications, from home automation to industrial control systems. Despite their small size, Raspberry Pi boards boast impressive capabilities, making them ideal for IoT projects.
Key Features of Raspberry Pi
- Compact and lightweight design, perfect for portable applications.
- Low power consumption, ensuring energy efficiency and extended usage.
- Support for multiple operating systems, providing flexibility in software selection.
- Extensive community support and resources, offering a wealth of knowledge and assistance.
- Affordable price point, making it accessible for hobbyists and professionals alike.
These features, combined with the ability to integrate with RemoteIoT platforms, make Raspberry Pi an excellent choice for IoT enthusiasts seeking to implement secure and efficient remote access solutions.
The Importance of SSH Key-Free Access
SSH (Secure Shell) is a cryptographic network protocol that secures communications between devices over unsecured networks. Traditionally, SSH access requires the use of public and private key pairs for user authentication, which, while secure, can be cumbersome for users requiring quick and easy access. SSH key-free access simplifies this process by eliminating the need for managing complex key pairs.
Instead of relying on keys, SSH key-free access often employs alternative authentication methods such as passwords or two-factor authentication (2FA). This approach streamlines the setup process without compromising security, offering users a balance between convenience and protection. By adopting SSH key-free access, users can enjoy seamless connectivity while maintaining the necessary security measures to protect their IoT devices.
Read also:What Is The Gerber Life College Plan And How Can It Help You Save For Education
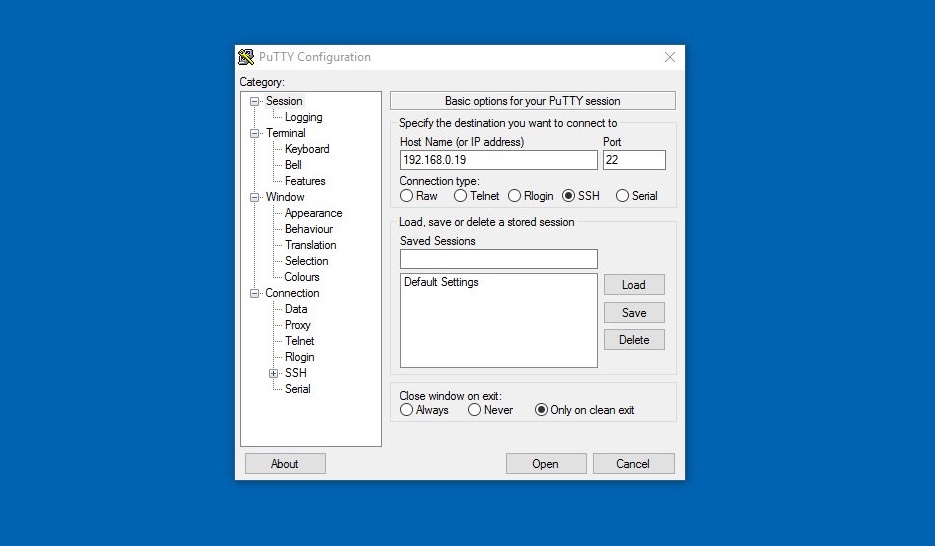
Step-by-Step Setup Guide
Preparing Your Raspberry Pi
Before configuring your Raspberry Pi for remote access, it's essential to ensure the device is properly set up and updated. Follow these steps to prepare your Raspberry Pi:
- Install the latest version of Raspberry Pi OS on your device.
- Connect your Raspberry Pi to a monitor, keyboard, and mouse for initial setup.
- Update the system using the following commands:
sudo apt update
sudo apt upgrade
Configuring RemoteIoT Platform
Once your Raspberry Pi is ready, proceed to configure the RemoteIoT platform. Here's how:
- Create an account on the RemoteIoT platform of your choice.
- Download and install the platform's software on your Raspberry Pi.
- Follow the platform's instructions to complete the setup process, ensuring all configurations align with your specific requirements.
Enhancing Security in RemoteIoT Platforms
Security remains a top priority in remote access solutions. To safeguard your RemoteIoT platform, consider implementing the following best practices:
- Utilize strong, unique passwords and enable two-factor authentication (2FA) to enhance account security.
- Regularly update your software and firmware to address vulnerabilities and ensure protection against emerging threats.
- Restrict access to authorized users only, minimizing the risk of unauthorized access.
- Monitor your system for suspicious activity and take immediate action if any anomalies are detected.
By adhering to these practices, you can significantly reduce the risk of security breaches and protect your IoT devices from potential threats.
Advantages of RemoteIoT Platforms
RemoteIoT platforms offer numerous benefits for businesses and individuals, transforming the way IoT devices are managed. Some key advantages include:
- Improved efficiency and productivity through seamless remote access and management capabilities.
- Cost savings by reducing the need for on-site visits and minimizing maintenance requirements.
- Enhanced security through advanced authentication and encryption methods, ensuring data protection.
- Scalability to accommodate growing IoT ecosystems, supporting expansion and innovation.
These benefits make RemoteIoT platforms an invaluable tool for anyone looking to leverage IoT technology effectively.
Overcoming Common Challenges
While RemoteIoT platforms offer significant advantages, users may encounter challenges during implementation. Common issues include complex setup processes, security concerns, and compatibility problems. To address these challenges, users can:
- Refer to the platform's documentation and support resources for guidance and troubleshooting.
- Implement robust security measures, such as 2FA and regular updates, to mitigate risks.
- Select platforms that offer broad compatibility with various devices and operating systems, ensuring seamless integration.
Practical Use Cases
RemoteIoT platforms have been successfully deployed across multiple industries, showcasing their versatility and potential. Some real-world applications include:
- Home automation systems for managing smart devices, enhancing convenience and energy efficiency.
- Industrial control systems for monitoring and managing equipment, improving operational efficiency.
- Agricultural applications for remote monitoring of crop conditions, optimizing resource utilization.
- Healthcare systems for remote patient monitoring and data collection, enhancing patient care and outcomes.
These examples highlight the diverse applications of RemoteIoT platforms and their ability to drive innovation across various sectors.
Best Practices for Deployment
To ensure a successful deployment of your RemoteIoT platform, follow these best practices:
- Carefully plan your deployment, considering factors such as device compatibility, network requirements, and scalability needs.
- Thoroughly test your setup before deploying it in a production environment to identify and resolve potential issues.
- Document your configuration and setup process for future reference, facilitating maintenance and troubleshooting.
- Stay informed about the latest advancements and updates in the IoT and RemoteIoT space, ensuring your system remains up-to-date and effective.
By following these practices, you can maximize the effectiveness of your RemoteIoT platform and achieve optimal results.
Emerging Trends in IoT Remote Access
The field of IoT remote access continues to evolve, driven by technological advancements and innovations. Key trends to watch include:
- Increased adoption of artificial intelligence (AI) and machine learning for predictive maintenance and automation, enhancing operational efficiency.
- Greater emphasis on cybersecurity to address emerging threats and protect sensitive data.
- Integration with 5G networks for faster, more reliable connectivity, enabling real-time monitoring and control.
- Development of new platforms and tools designed to simplify remote access and management, making IoT technology more accessible.
By staying informed about these trends, businesses and individuals can leverage the latest advancements in IoT technology to drive innovation and growth.
Kesimpulan
In conclusion, RemoteIoT platforms represent a powerful and flexible solution for managing IoT devices remotely. By integrating these platforms with Raspberry Pi, users can create customized solutions that meet their specific needs while maintaining a high level of security. SSH key-free access simplifies the setup process, making remote IoT management accessible to a broader audience.
We encourage you to explore the possibilities of RemoteIoT platforms and consider implementing them in your IoT projects. Share your thoughts and experiences in the comments section below, and for more insights into IoT and related topics, explore our other articles on the site.
Thank you for reading, and happy tinkering!