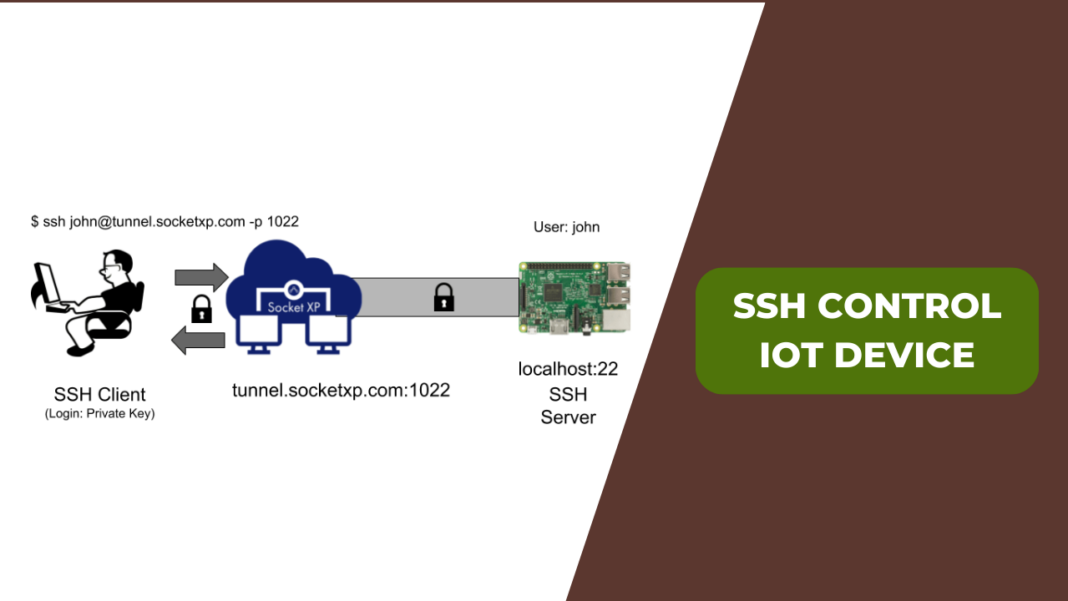
Mastering Secure Remote IoT Management With SSH
In today's fast-paced world of the Internet of Things (IoT), effectively and securely managing remote devices has become an essential task for businesses and developers alike. Secure Shell (SSH) is not merely a buzzword but a cornerstone technology that ensures reliable connectivity, robust security, and unmatched flexibility. As IoT devices increasingly integrate into our daily lives, understanding SSH and its applications has become indispensable for anyone working in this dynamic field.
SSH, or Secure Shell, is a cryptographic network protocol designed to facilitate secure communication over unsecured networks. It plays a pivotal role in remote management, empowering administrators to control IoT devices from anywhere in the world with minimal risk of unauthorized access. In an era marked by increasingly sophisticated cyber threats, the importance of SSH cannot be overstated.
This comprehensive guide will delve into the intricacies of utilizing SSH for managing remote IoT devices, covering everything from foundational concepts to advanced techniques. Whether you're a beginner eager to grasp the basics or an experienced professional seeking to refine your skills, this article aims to provide actionable insights and valuable knowledge to enhance your expertise.
Read also:Discovering The Most Dangerous Zodiac Sign When Angry Unveiling Astrological Insights
Table of Contents
- Introduction to SSH and IoT
- Understanding SSH Basics
- Overview of IoT Devices
- Security Considerations for IoT Devices
- Implementing SSH for IoT Devices
- Benefits of Using SSH for Remote IoT Management
- Tools and Software for SSH in IoT
- Troubleshooting Common SSH Issues
- Best Practices for SSH in IoT
- The Future of SSH in IoT
- Conclusion
Understanding SSH and IoT: A Powerful Combination
Why SSH is Essential in IoT
SSH stands as a foundational technology for secure remote access, making it indispensable in the realm of IoT. With IoT devices often deployed in remote and inaccessible locations, administrators rely heavily on SSH to perform essential tasks such as configuration, monitoring, and troubleshooting without the need for physical presence. This section explores the critical role SSH plays in IoT and how it addresses common challenges faced in the industry.
Key Features of SSH for IoT
Among its many features, SSH offers robust encryption, secure authentication, and data integrity checks, ensuring seamless and secure communication between devices. These capabilities are particularly advantageous for IoT devices, which often operate under resource constraints and are vulnerable to various cyber threats. By leveraging SSH, businesses can safeguard sensitive data, ensuring operational continuity and trust with end-users.
Exploring the Fundamentals of SSH
Before diving into its application within the IoT ecosystem, it's crucial to understand the basic principles of SSH. This section covers fundamental concepts, including how SSH operates, its key components, and the role of public and private keys in establishing secure connections. Grasping these basics will provide a solid foundation for effectively utilizing SSH in IoT environments.
How SSH Ensures Secure Communication
SSH operates by establishing a secure channel over unsecured networks. It employs advanced encryption algorithms to protect data during transmission, ensuring that even if intercepted, the information remains unreadable to unauthorized parties. This mechanism forms the backbone of secure remote management in IoT.
Navigating the Diverse World of IoT Devices
The IoT ecosystem spans a vast array of devices, ranging from smart home appliances to sophisticated industrial sensors. Each device type presents unique requirements and challenges when it comes to remote management. This section provides an overview of common IoT devices and their specific management needs, offering insights into tailoring SSH implementation for various applications.
Types of IoT Devices and Their Management Needs
- Consumer Devices: Including smart thermostats, lighting systems, and security cameras, these devices require user-friendly interfaces and seamless integration into home networks.
- Industrial Devices: Sensors, actuators, and control systems used in manufacturing plants demand robust security and reliability to ensure smooth operations.
- Enterprise Devices: Networked devices deployed in corporate environments for monitoring and automation must balance performance with security to meet stringent enterprise standards.
Addressing Security Challenges in IoT
Security remains a top priority when managing IoT devices remotely. This section examines the potential vulnerabilities associated with IoT devices and how SSH serves as a powerful tool to mitigate these risks, ensuring the integrity and confidentiality of data.
Read also:Exploring The Remarkable World Of Ts Luana A Digital Content Creator Extraordinaire
Common IoT Security Threats and SSH Solutions
IoT devices face numerous security threats, ranging from unauthorized access to data breaches. By implementing SSH, administrators can significantly reduce these risks through secure communication channels and robust authentication mechanisms. This section outlines specific strategies for leveraging SSH to fortify IoT security.
Setting Up SSH for IoT Devices: A Step-by-Step Guide
Configuring SSH for IoT devices involves several critical steps, from installing the SSH server to generating key pairs and configuring firewall rules. This section provides a detailed, step-by-step guide to implementing SSH in an IoT environment, ensuring secure and efficient remote management.
Key Steps for SSH Implementation
- Install an SSH Server: Begin by installing an SSH server on the IoT device to enable secure remote access.
- Generate Public and Private Keys: Create key pairs for authentication, ensuring secure and passwordless access to the device.
- Configure Firewall Rules: Adjust firewall settings to allow SSH traffic while blocking unauthorized access.
- Test the Connection: Verify the setup by testing the connection to ensure secure and reliable access.
Unlocking the Advantages of SSH in IoT
Integrating SSH into your IoT management strategy offers numerous advantages, including enhanced security, increased flexibility, and cost-effectiveness. This section highlights the key benefits of using SSH for remote IoT management, emphasizing its transformative impact on modern IoT ecosystems.
Enhancing Security with SSH
SSH provides end-to-end encryption, making it nearly impossible for attackers to intercept or manipulate data during transmission. This level of security is vital for protecting sensitive information and maintaining trust with end-users, especially in critical IoT applications.
Exploring Tools and Software for SSH in IoT
A variety of tools and software solutions are available to facilitate SSH implementation in IoT environments. This section reviews some of the most popular options, such as OpenSSH and PuTTY, offering insights into their features and capabilities to help you choose the best solution for your needs.
OpenSSH: A Leading Solution for IoT
OpenSSH is a widely adopted open-source software suite that provides robust SSH capabilities. Compatible with various operating systems, OpenSSH offers extensive customization options, making it a preferred choice for many IoT developers seeking secure and flexible remote management solutions.
Resolving Common SSH Issues in IoT
Even with a well-planned setup, challenges can arise when using SSH for IoT devices. This section addresses common issues, such as connection failures, and provides practical solutions to help administrators quickly and efficiently resolve these problems.
Addressing Connection Issues
Connection failures are among the most frequent issues encountered when using SSH for IoT devices. These problems can stem from misconfigured settings, network disruptions, or incorrect key pairs. By adhering to best practices and conducting regular maintenance, administrators can minimize the occurrence of these issues, ensuring smooth and uninterrupted operations.
Adopting Best Practices for SSH in IoT
To fully leverage the benefits of SSH in IoT, it's essential to follow established best practices. This section outlines key strategies for ensuring secure and efficient remote management of IoT devices, empowering administrators to optimize their workflows and enhance system performance.
The Importance of Regular Updates
Keeping software and firmware up-to-date is critical for maintaining security and functionality. Regular updates not only patch vulnerabilities but also introduce new features that enhance the overall performance of SSH in IoT environments, ensuring long-term reliability and effectiveness.
The Evolving Role of SSH in IoT
As technology continues to advance, the role of SSH in IoT is poised to expand significantly. This section explores emerging trends and innovations that are shaping the future of SSH in the IoT landscape, offering a glimpse into how this powerful tool will continue to evolve and adapt to meet the needs of modern IoT ecosystems.
Revolutionizing SSH with AI and Machine Learning
The integration of artificial intelligence (AI) and machine learning (ML) is set to transform how SSH is utilized in IoT. By leveraging these cutting-edge technologies, administrators can automate routine tasks, predict potential issues, and optimize system performance, leading to more efficient and secure remote management solutions.
Conclusion: Embrace SSH for Secure IoT Management
In conclusion, SSH is a transformative tool for managing remote IoT devices, offering unparalleled security, flexibility, and cost-effectiveness. By mastering the fundamentals of SSH and adhering to best practices, businesses and developers can ensure secure and efficient management of their IoT devices. We invite readers to share their experiences and insights in the comments section and explore additional resources on our site for further learning and exploration.
For additional reading, consider exploring authoritative sources such as SSH.com and NIST, which provide comprehensive guides and updates on SSH and IoT security, empowering you to stay informed and ahead in this rapidly evolving field.