Mastering Secure IoT Device Management With VPC And SSH On AWS
In today's rapidly advancing world of cloud computing, securing remote IoT devices through the integration of Virtual Private Cloud (VPC) and Secure Shell (SSH) on Amazon Web Services (AWS) is a necessity for modern businesses. As organizations increasingly adopt IoT technologies, the demand for robust networking and security solutions grows. RemoteIoT VPC SSH AWS offers a sophisticated set of tools that enable seamless and secure communication between IoT devices and cloud-based systems, ensuring data integrity and operational efficiency.
This comprehensive guide will explore the complexities of setting up and managing a VPC for remote IoT devices, utilizing SSH for secure connections, and optimizing AWS resources to achieve peak performance. Whether you're just starting your journey into cloud networking or are an experienced professional seeking to enhance your skills, this guide will provide valuable insights and actionable advice.
Throughout this article, we will examine fundamental concepts, best practices, and advanced strategies to help you fully leverage the capabilities of RemoteIoT VPC SSH AWS. By the end, you will possess a thorough understanding of designing, implementing, and maintaining secure IoT networks within the AWS ecosystem.
Read also:Why You Should Join Wewillwritecom Today Unlock Your Writing Potential
Exploring the RemoteIoT VPC SSH AWS Framework
The RemoteIoT VPC SSH AWS framework is a powerful solution that combines the functionalities of IoT devices, Virtual Private Clouds (VPCs), Secure Shell (SSH), and Amazon Web Services (AWS). This integration empowers organizations to establish secure and controlled connections with remote IoT devices within an isolated network environment, enhancing both security and operational efficiency.
What Exactly is a VPC in AWS?
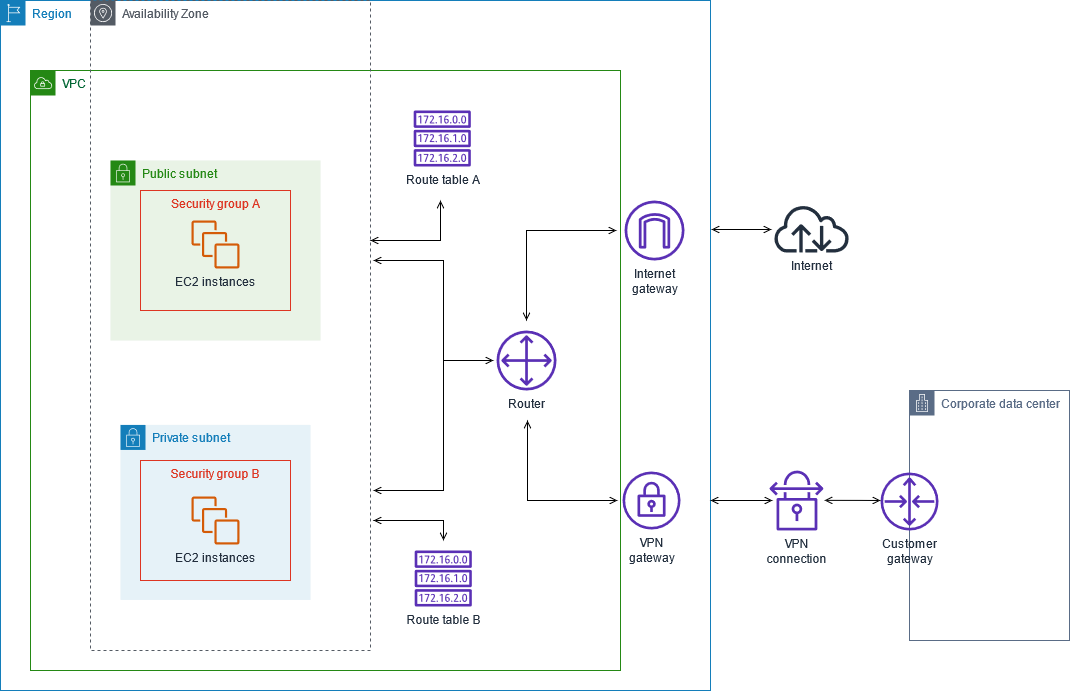
A Virtual Private Cloud (VPC) in AWS refers to a logically isolated section of the AWS Cloud where you can deploy AWS resources in a virtual network tailored to your specifications. With VPC, you gain complete control over your networking environment, including the ability to define IP address ranges, create subnets, manage route tables, and configure security settings.
- VPC provides a secure and highly customizable networking environment for your AWS resources, ensuring data protection and compliance with security standards.
- You can establish multiple subnets within a VPC, enabling you to segment your network based on specific organizational requirements and enhance security by isolating critical components.
- VPC supports both public and private subnets, giving you the flexibility to control access to your resources and ensure that sensitive data remains protected from unauthorized access.
The Importance of SSH in Establishing Secure Connections
Secure Shell (SSH) is a cryptographic network protocol designed to secure communications between devices over unsecured networks. In the context of RemoteIoT VPC SSH AWS, SSH is essential for establishing secure and encrypted connections between IoT devices and cloud-based systems, safeguarding data transmissions against potential threats.
- SSH encrypts all data transmitted between devices, ensuring confidentiality and integrity of information exchanged over the network.
- It offers robust authentication mechanisms to verify the identities of devices and users, preventing unauthorized access and potential security breaches.
- SSH supports a wide range of encryption algorithms, providing flexibility and ensuring compliance with the latest security standards and best practices.
Building a VPC Tailored for Remote IoT Devices
Creating a VPC specifically designed for remote IoT devices involves several critical steps. This section will guide you through the process, ensuring your IoT network is secure, efficient, and scalable to meet future demands.
Step 1: Establish Your VPC Parameters
Begin by defining the IP address range for your VPC. This range will dictate the size of your network and the number of devices that can be connected, making it essential to carefully plan based on your organization's current and anticipated needs.
Step 2: Segment Your VPC with Subnets
Divide your VPC into subnets to organize your network architecture effectively and enhance security. Public subnets can be utilized for devices requiring internet access, while private subnets can be reserved for internal communication, ensuring sensitive data remains protected.
Read also:Is Megan Moroney A Liberal Exploring Her Political Identity
Step 3: Configure Security Groups for Enhanced Protection
Security groups act as virtual firewalls for your instances, controlling inbound and outbound traffic. Define precise rules specifying which traffic is allowed to enter or leave your instances, ensuring only authorized communication occurs and minimizing the risk of potential security threats.
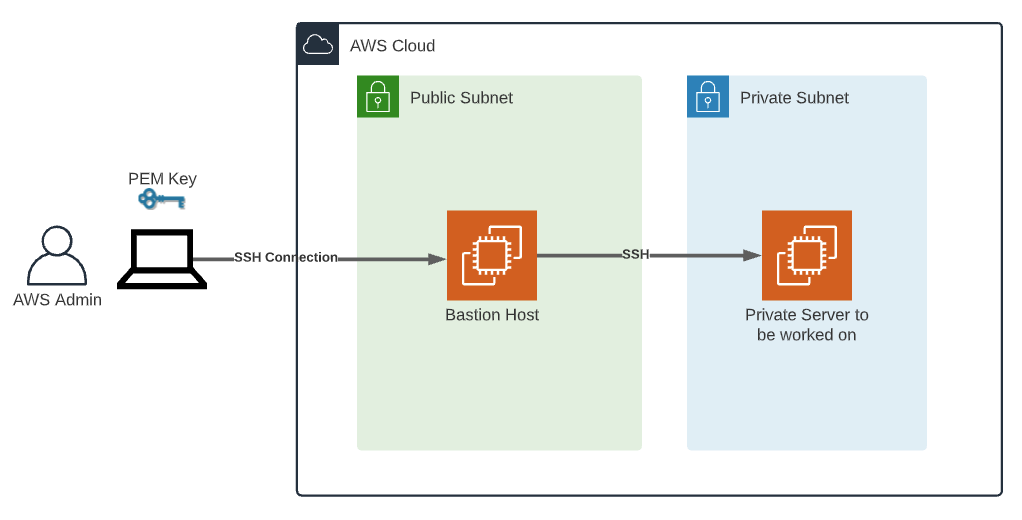
Deploying SSH for Secure IoT Connections
After setting up your VPC, the next step is implementing SSH to secure connections between your IoT devices and AWS resources. This section will guide you through the process, ensuring your network remains secure and efficient.
Generating SSH Keys for Secure Authentication
SSH keys are fundamental for secure authentication. Follow these steps to generate SSH keys:
- Use a trusted tool like ssh-keygen to create a key pair, ensuring strong encryption and secure communication.
- Store the private key securely on your local machine, protecting it from unauthorized access and potential breaches.
- Upload the public key to your AWS instances or IoT devices, enabling secure authentication and facilitating seamless communication.
Establishing SSH Connections with IoT Devices
Connecting to your IoT devices via SSH involves several critical steps:
- Ensure your device is properly configured to accept SSH connections, verifying all necessary settings and configurations are in place.
- Utilize an SSH client to connect to the device's public IP address or DNS name, ensuring secure and reliable communication.
- Authenticate using the private key you generated earlier, ensuring secure access and protecting against unauthorized intrusions.
Best Practices for Enhancing RemoteIoT VPC SSH AWS Security
Implementing best practices is crucial for maximizing the security and efficiency of your RemoteIoT VPC SSH AWS setup. Follow these guidelines to ensure your network remains secure and performs optimally.
Regularly Update Security Settings
Maintain the highest level of security by regularly updating your security groups and network ACLs. Monitor traffic patterns closely and adjust rules as needed to address evolving security threats and ensure optimal performance.
Implement Multi-Factor Authentication (MFA)
Enhance the security of your SSH connections by implementing multi-factor authentication (MFA). This additional layer of protection significantly reduces the risk of unauthorized access, safeguarding your network and sensitive data from potential breaches.
Monitor Network Activity for Proactive Security
Utilize AWS CloudWatch and other advanced monitoring tools to track network activity within your VPC. This proactive approach enables you to promptly identify and respond to any suspicious behavior, ensuring your network remains secure and operational at all times.
Advanced Techniques for Optimizing RemoteIoT VPC SSH AWS
For those seeking to elevate their RemoteIoT VPC SSH AWS setup, consider implementing these advanced techniques:
Automating SSH Key Management for Consistency
Automate the generation and distribution of SSH keys using tools like AWS Systems Manager or third-party solutions. This approach minimizes the risk of human error and ensures consistent key management across your network, enhancing both security and operational efficiency.
Leveraging VPC Endpoints for Enhanced Connectivity
VPC Endpoints enable you to connect your VPC to supported AWS services without requiring an internet gateway, NAT device, or VPN connection. This significantly improves both security and performance by keeping traffic within the AWS network, reducing latency, and enhancing data protection.
Addressing Common Challenges and Solutions
While RemoteIoT VPC SSH AWS offers numerous advantages, it also presents certain challenges. Below are some common issues and their respective solutions:
Configuring Security Groups: A Potential Hurdle
Solution: Start with default security group settings and gradually refine them based on your specific requirements. Refer to AWS documentation for guidance on best practices, ensuring your security configurations are both effective and compliant.
Resolving SSH Connectivity Issues
Solution: Verify that your security groups and network ACLs allow SSH traffic, ensuring no unnecessary restrictions are in place. Check that your SSH keys are correctly configured and that your device's firewall settings are not blocking connections, enabling seamless and secure communication.
Case Studies: Real-World Applications of RemoteIoT VPC SSH AWS
Explore real-world examples of organizations successfully implementing RemoteIoT VPC SSH AWS solutions to enhance their operations and achieve their business objectives:
Case Study 1: Revolutionizing Smart Agriculture
Agricultural company XYZ implemented RemoteIoT VPC SSH AWS to manage a network of soil moisture sensors. By securely connecting these devices to AWS, they were able to collect and analyze data in real-time, optimizing irrigation schedules and significantly improving crop yields, demonstrating the transformative potential of IoT in agriculture.
Case Study 2: Streamlining Industrial Automation
Manufacturing firm ABC adopted RemoteIoT VPC SSH AWS to monitor and control a fleet of robotic arms. This setup enabled them to streamline operations, minimize downtime, and enhance overall efficiency, showcasing the power of IoT in modern industrial settings.
Future Trends Shaping RemoteIoT VPC SSH AWS
As technology continues to evolve, several trends are shaping the future of RemoteIoT VPC SSH AWS:
- Increased adoption of edge computing to reduce latency and enhance performance, enabling real-time data processing and decision-making.
- Advancements in artificial intelligence (AI) and machine learning (ML) for predictive maintenance and anomaly detection, improving operational efficiency and reducing costs.
- Enhanced security measures to address emerging threats and vulnerabilities, ensuring the protection of sensitive data and maintaining the integrity of IoT networks.
Conclusion
Mastering RemoteIoT VPC SSH AWS is vital for organizations seeking to harness the full potential of cloud computing in their IoT deployments. By adhering to the guidelines and best practices outlined in this article, you can create a secure, efficient, and scalable networking environment for your remote IoT devices, driving innovation and achieving business success.
We invite you to share your thoughts and experiences in the comments section below. If you found this article valuable, consider sharing it with your network. For additional in-depth guides and resources on cloud computing and IoT solutions, explore our other articles and continue expanding your knowledge.
Table of Contents
- Exploring the RemoteIoT VPC SSH AWS Framework
- Building a VPC Tailored for Remote IoT Devices
- Deploying SSH for Secure IoT Connections
- Best Practices for Enhancing RemoteIoT VPC SSH AWS Security
- Advanced Techniques for Optimizing RemoteIoT VPC SSH AWS
- Addressing Common Challenges and Solutions
- Case Studies: Real-World Applications of RemoteIoT VPC SSH AWS
- Future Trends Shaping RemoteIoT VPC SSH AWS
- Conclusion