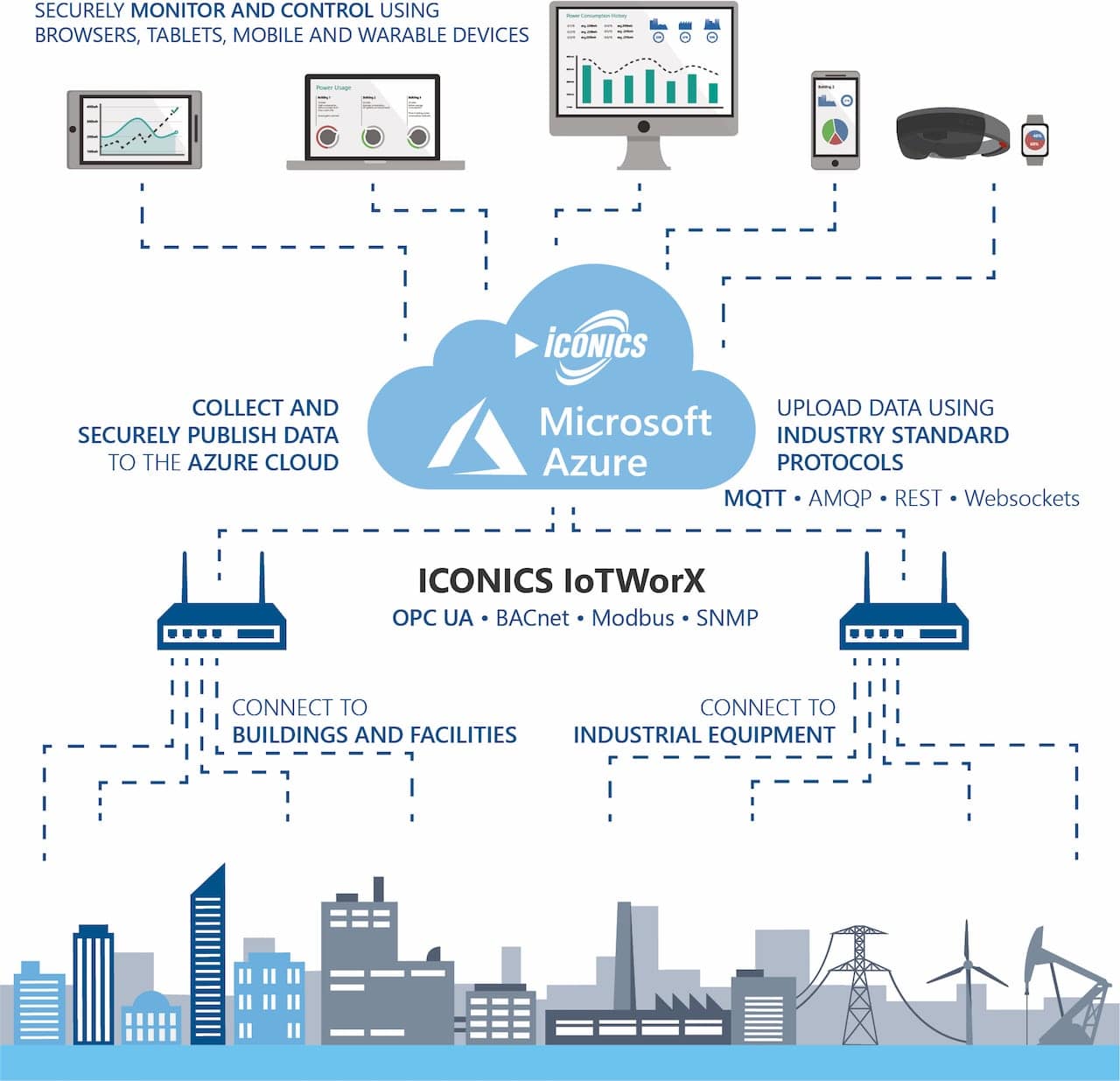
Enhancing Security For Remote IoT VPC Connections
In today's interconnected digital landscape, ensuring the secure connection of remote IoT devices within a Virtual Private Cloud (VPC) is a critical priority for businesses. The rapid expansion of the Internet of Things (IoT) has created exciting opportunities, yet it also poses significant security challenges. This guide will delve into the best practices and strategies to fortify your remote IoT VPC, ensuring both security and operational efficiency.
As organizations increasingly depend on IoT devices to optimize their operations, the necessity to safeguard sensitive data and uphold system integrity has never been more crucial. By recognizing the associated risks and implementing comprehensive security measures, businesses can effectively mitigate potential threats and ensure uninterrupted connectivity.
This in-depth guide will walk you through the essential steps and techniques for securely connecting remote IoT VPCs, offering valuable advice and actionable insights to help you establish a secure network infrastructure that meets modern demands.
Read also:Exploring Elon Musks Partners And Kids A Comprehensive Look
Table of Contents
- Introduction to Securely Connecting Remote IoT VPC
- Understanding IoT and Its Importance
- What is a Virtual Private Cloud (VPC)?
- Key Strategies for Securing Remote IoT VPC
- Best Practices for IoT Security
- Common Risks and Threats in IoT VPC
- Essential Tools for Securing IoT VPC
- Optimizing Network Design for Enhanced Security
- Compliance and Regulatory Considerations for IoT VPC
- Emerging Trends in IoT Security
- Conclusion and Next Steps
Introduction to Securely Connecting Remote IoT VPC
Establishing a secure connection between IoT devices and a Virtual Private Cloud (VPC) remotely demands a well-structured approach to ensure robust data security and network reliability. This section will explore the foundational aspects of securely connecting IoT devices and highlight its significance for contemporary businesses.
With the exponential growth of IoT adoption, organizations must prioritize cybersecurity to safeguard their infrastructure from cyber threats. A secure IoT VPC connection not only strengthens data protection but also enhances operational efficiency, empowering businesses to thrive in an increasingly digital world.
To achieve this, it is imperative to implement advanced security protocols and adhere to industry standards. By comprehending the core principles of securely connecting IoT devices, businesses can construct a resilient network architecture that aligns with their long-term strategic objectives.
Understanding IoT and Its Importance
The Internet of Things (IoT) encompasses a network of physical devices embedded with sensors, software, and connectivity features, enabling them to exchange data and execute automated tasks. IoT has revolutionized industries by boosting productivity, enabling real-time monitoring, and transforming business processes.
Key Benefits of IoT
- Significantly improved operational efficiency
- Advanced real-time data analytics capabilities
- Enhanced customer experiences through personalized interactions
- Substantial cost savings through automation and streamlined processes
As businesses increasingly rely on IoT devices, ensuring secure connectivity becomes a cornerstone of operational success. By integrating IoT with a VPC, organizations can harness the power of cloud computing while maintaining stringent security measures to protect sensitive information.
What is a Virtual Private Cloud (VPC)?
A Virtual Private Cloud (VPC) represents a secure and isolated segment within a cloud environment, where businesses can deploy applications and store sensitive data. VPCs offer enhanced security features, including network access control, encryption, and traffic filtering, making them an ideal solution for securely connecting IoT devices.
Read also:Why You Should Join Wewillwritecom Today Unlock Your Writing Potential
Advantages of Using a VPC
- Heightened security through network isolation
- Flexible network configuration to meet diverse business needs
- Scalability to accommodate growing demands and evolving requirements
- Cost-effective resource management for optimized budget allocation
By leveraging VPCs, businesses can create a secure ecosystem for their IoT devices, ensuring that sensitive data remains protected from unauthorized access and potential breaches.
Key Strategies for Securing Remote IoT VPC
Securing IoT devices within a VPC requires a comprehensive, multi-layered approach to address potential vulnerabilities and mitigate risks effectively. Below are some pivotal strategies to enhance the security of your IoT VPC connection:
1. Implement Robust Authentication Mechanisms
Employ advanced authentication protocols, such as OAuth 2.0 or JSON Web Tokens (JWT), to ensure that only authorized devices and users can access the VPC. This approach significantly reduces the risk of unauthorized access and enhances overall security.
2. Enable Encryption for Data Transmission
Encrypt all data transmitted between IoT devices and the VPC using robust protocols like TLS or SSL. This measure prevents data interception and tampering, ensuring the integrity and confidentiality of sensitive information.
3. Regularly Update Firmware and Software
Keep IoT device firmware and software up to date to address vulnerabilities and incorporate the latest security features. Regular updates are essential for maintaining a secure and resilient IoT VPC environment.
Best Practices for IoT Security
Adopting best practices is fundamental to maintaining a secure IoT VPC environment. Below are some practical tips to enhance your security posture and protect your network infrastructure:
1. Segment Your Network
Divide your network into smaller, isolated segments to contain IoT devices and limit the spread of potential threats. Network segmentation reduces the attack surface and minimizes the impact of security breaches.
2. Monitor Network Traffic
Deploy network monitoring tools to detect and respond to suspicious activities in real-time. Proactive monitoring enables swift identification and resolution of security incidents, enhancing overall network resilience.
3. Conduct Regular Security Audits
Perform periodic security assessments to identify vulnerabilities and implement necessary improvements. Regular audits ensure that your security measures remain effective and aligned with evolving threat landscapes.
Common Risks and Threats in IoT VPC
Despite the numerous benefits of IoT, connecting devices to a VPC introduces several risks and threats that must be carefully managed. Understanding these challenges is essential for developing effective security strategies.
1. Data Breaches
Unauthorized access to sensitive data can result in financial losses, reputational damage, and legal consequences. Implementing robust security measures is crucial for preventing data breaches and protecting valuable information.
2. Device Compromise
Compromised IoT devices can serve as entry points for attackers to infiltrate the VPC, jeopardizing the entire network. Ensuring the security of individual devices is vital for safeguarding the broader infrastructure.
3. Denial of Service (DoS) Attacks
Attacks aimed at overwhelming the network can disrupt operations, causing downtime and financial losses. Implementing robust defenses against DoS attacks is essential for maintaining operational continuity.
Essential Tools for Securing IoT VPC
Several tools and technologies can assist businesses in enhancing the security of their IoT VPC connections. Below are some of the most effective tools available:
1. Firewalls
Deploy firewalls to control inbound and outbound traffic, ensuring that only legitimate connections are permitted. Firewalls play a critical role in protecting the network from unauthorized access and potential threats.
2. Intrusion Detection Systems (IDS)
Utilize IDS to monitor network traffic for signs of malicious activity and alert administrators of potential threats. Early detection and response are vital for mitigating security risks and minimizing damage.
3. Security Information and Event Management (SIEM)
Implement SIEM solutions to aggregate and analyze security data from various sources for comprehensive threat detection. SIEM tools provide valuable insights into network activity, enabling proactive security management.
Optimizing Network Design for Enhanced Security
A meticulously designed network architecture is essential for ensuring the security of IoT VPC connections. By adhering to best practices in network design, businesses can minimize vulnerabilities and enhance resilience against potential threats.
1. Adopt a Zero-Trust Model
Embrace a zero-trust security approach, verifying every connection and device before granting access. This strategy eliminates implicit trust and strengthens network security.
2. Implement Micro-Segmentation
Utilize micro-segmentation to create smaller, isolated zones within the network, reducing the attack surface and limiting the impact of security breaches. Micro-segmentation enhances network control and improves overall security.
3. Automate Security Processes
Leverage automation tools to streamline security operations and reduce the risk of human error. Automation enhances efficiency, ensures consistency, and enables rapid response to emerging threats.
Compliance and Regulatory Considerations for IoT VPC
Businesses must comply with relevant regulatory frameworks when securing IoT VPC connections. Below are some of the key compliance standards to consider:
1. General Data Protection Regulation (GDPR)
Ensure adherence to GDPR requirements for protecting personal data in the European Union. Compliance with GDPR safeguards sensitive information and avoids legal penalties.
2. Health Insurance Portability and Accountability Act (HIPAA)
Follow HIPAA guidelines to safeguard sensitive health information in the healthcare industry. HIPAA compliance is essential for maintaining patient privacy and trust.
3. Payment Card Industry Data Security Standard (PCI DSS)
Adhere to PCI DSS standards for securing payment card data in the financial sector. Compliance with PCI DSS ensures the protection of financial transactions and sensitive customer information.
Emerging Trends in IoT Security
As technology continues to evolve, new trends in IoT security are emerging to address emerging threats and challenges. Below are some key trends to watch:
1. Artificial Intelligence (AI) and Machine Learning (ML)
AI and ML are being leveraged to enhance threat detection and response capabilities in IoT networks. These technologies enable predictive analytics and automated responses, improving overall security effectiveness.
2. Blockchain Technology
Blockchain offers a decentralized approach to securing IoT transactions and ensuring data integrity. By leveraging blockchain, businesses can enhance trust and transparency in IoT ecosystems.
3. Edge Computing
Edge computing reduces latency and enhances security by processing data closer to the source. This approach minimizes the reliance on centralized cloud infrastructure, improving performance and security.
Conclusion and Next Steps
Securing remote IoT VPC connections is essential for protecting sensitive data and maintaining operational efficiency in today's digital landscape. By implementing the strategies and best practices outlined in this guide, businesses can establish a robust security framework that safeguards their IoT infrastructure against evolving threats.
We encourage readers to take action by reviewing their current security measures and implementing necessary improvements. Share your thoughts and experiences in the comments below, and explore additional resources on our site for further insights into IoT security and related topics.